Mobile network hacking is one of the common issues these days, but that doesn't mean your computer is safe from hackers. Sometimes small fly's searching for free wireless network hacked your computer without warning.
If you're an advanced user of Mac OS X, it's very likely that you know what Terminal.app is. If you're not, the Terminal is an application included in every version of OS X into the Utilities folder which provides a command line interface to manually control your Mac. In this roundup I've collected the best links about Terminal.app: you'll find the best commands, hacks and tips to. Metasploit Best collection of exploit tools. Rather than calling Metasploit a collection of exploit. CleanMyMac 4.6.14 Crack Mac OS X With Activation Number Foxit PhantomPDF 10.1.0.37527 Crack Plus Activation Code Download Camtasia Studio 2020.0.8 Crack (Latest+Keygen) Full Version.
If you're thinking hackers did not hack your computer machine because you're a small fly nobody wants to hack you. That's your biggest mistake hackers always try to increase IP database through hacking computer.
When hackers, hack any website or server they generally do it by opening that particular site to millions of IP address and hence the server in cash. So you've to check if you're being targeted by the hacker or if on your mac there is any backdoor from which you're monitored.
If you questioning your self 'How to tell If your mac has been remotely accessed' by hackers. If you've felt your computer has been hacked you can easily check it and prevent using simple tools and software such as installing anti-virus on your Mac.
The answer is simple, there some ways from which you can easily determine your computer is hacked.
1 # Can I Tell If My Mac Has Been Hacked
To determine if your mac has been already hacked by hackers you have to know if things. First of all, you've to spot some sign of possible hacking.
You'll have to consider whether anything out of the usual is happening on your notebook. You know how your computer runs better than anyone else. If you've noticed anything usual after starting your MacBook. The weird sign includes.
- When you try to open any file but it won't open.
- Any Program automatically starts without running it.
- You cannot access any file or program protected by password setup by you.
- When you're not using your computer but still sometimes its connect to the internet automatically.
- File contents have been changed but your not who change them
- Your Printer not working but all look fine.
- The wired warring message shows up on the screen.
- Go online and check your online account passwords.
There are lots of signs from which you can easily detect your computer is hacked by somebody or there is a backdoor on your computer which remotely accessed by the hacker.

2 # Go online to check your Online Accounts through Private Browser
When you try to login into your online account such as Email Account you see a password failure. If you're feeling you're already hacked then, in this case, check your online account using a private browser. Because private browsing is safe and secure.
You can also notice if your network connection is redirected to another IP address or computer. Adobe acrobat for mac os 9 2. Lots of small hackers try to hack network to enjoy free internet but they can also remotely control your computer.
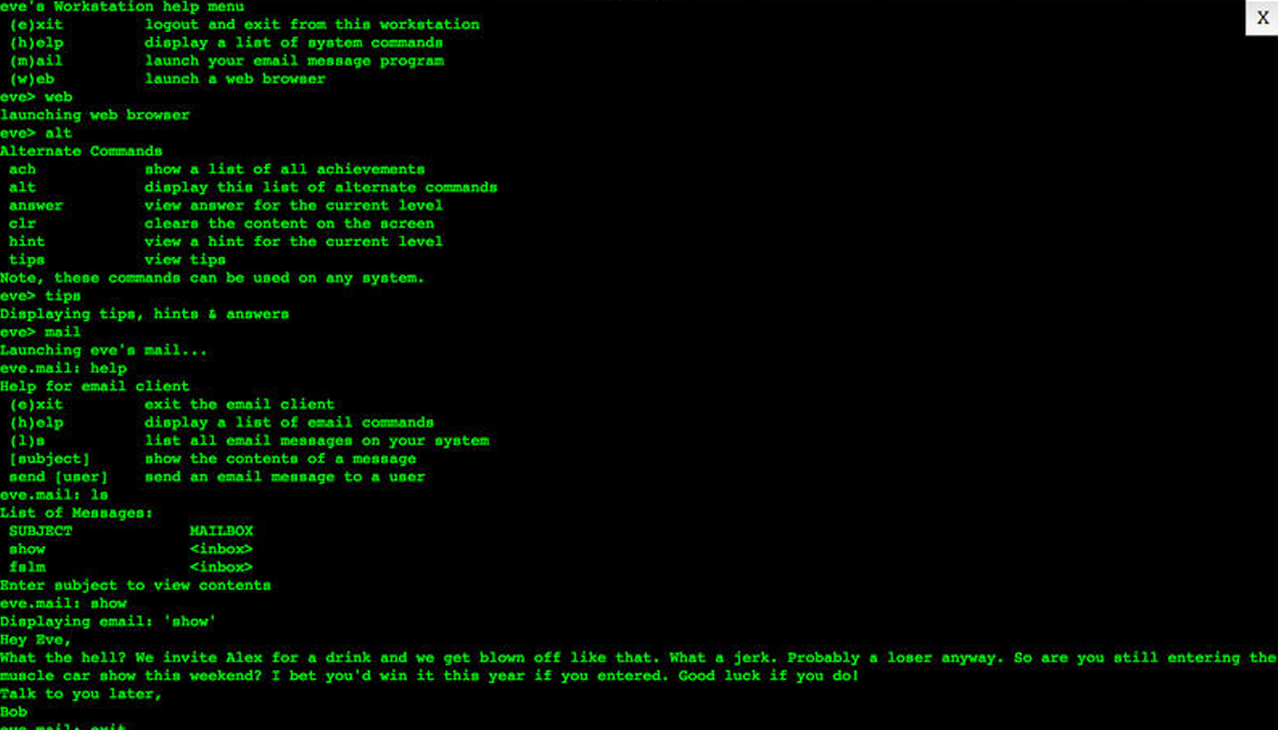
When you're browsing through the web browser you may also see an extra browser open up automatically without doing anything. If you own a domain for your website or blog you can access it after getting hacked.
3 # Anti-Virus Stop Working When Mac Computer Has Been Hacked
In Mac, if you already installed an anti-virus then this the best thing you've done to secure notebook. Oni chichi sub indo. To find out if your mac address has been hacked. You can easily check it out by scanning your Mac.
Usually, Mac users have to scan its system regularly to know if check anything usual such as the trojan virus. Trojan Virus is the virus created by hackers these viri contain backdoor or the spirits and command lines to open hidden gateways on your computer.
If you notice lots of trojan virus on your computer on the regular scan it is also a sign that your mac has been hacked.
4 # Check All Accounts Created By You on Mac Using Command Line
If you're thinking how would I know if my mac has been hacked into. Have you notice someone has seen your information and conversation on your computer. According to hackers, it is easier to hack mac in comparison to PC.
There are lots of mac terminal hack commands with the help of which hackers entered into your computer. But you can also use a command line to determine whether your Mac has been used without your authorization.
Login into your Mac OS notebook using for the regular account
Click on Applications > Utilities > Terminal
In Terminal (Command Prompt). Enter this command line 'sudo -l'.
Press Enter and then type account password and again press Enter.
Again in Terminal type following command line to open up the complete list of all accounts created on your Mac.
dscl . list /users
Press the 'Enter' button
Now you can easily check a complete list of account on your Mac OS computer. Check whether any account is created on Mac without your permission. If your mac is hacked there are additional accounts created by hackers.
In this last step, check whether an account is misused by any hacker. Type gave the following command line on Terminal
last
Hit 'Enter' now you can see each account on Mac last login date and time. Check out if there is an account which recently login without your permission.
If you've ever asked yourselves 'Which is the best OS for hacking in 2020?' than you're exactly where you should be, in your room, and on this exact page!
Security and Hacking has always been a passion of mine, and I'm sure you too have wanted to become a hacker at least at some point of your life, for some duration of time at least.
So, here I bring to you the 11 best Kali Linux Distro for hacking, well no they won't make you an expert 'hacker', that's something you'll have to work hard for, but these definitely will get you the tools and equipment you need to become so.
11 Best OS for Hacking in 2020
In case you're totally new to this, these hacking Linux distros are simply operating systems or more like versions of operating systems, locked and loaded with all the weapons you'll ever need to test the security and stability of whatever you're testing.
Try to use them to secure your computer or network rather than break into someone else's.
So here's the arsenal folks, 9 best OS for hacking (don't forget to check out #9).
1. Kali Linux
I believe not many of you here will even debate this, I mean even a hacker, who isn't a hacker, and hasn't ever wanted to be one, has heard of Kali Linux, isn't that right? It's arguably the best OS for hacking hands down!
Kali is designed and distributed by Offensive Security Ltd. as a re-write for Backtrack which was more of a forensic Linux distribution tool rather than a hacker's hammer.
Now before I say anything else, let me just say like for everything else on the planet, there are lovers, and haters for Kali, both with their own set of logics and reasons, and the 'I'm right' game goes on.
Mac Os X For Hackers
But, I personally love Kali for some basic reasons, it has 600+ pen-testing tools for starters, it's open-source, and it uses a single-root account by default, as most of the tools on Kali need highest level of privileges so it just seemed logical and time-saving (Although it has its downsides).
It's supported not only on computers with x86 wireframes, and ARM architectures, but also on smartphones including the Nexus series, One Plus One and some others!
Bottomline, Kali is designed for pen-testers and hackers; most of the tools need to be used from shell and there isn't a lot of GUI, but that's the beauty of it, you can't claim to climb the mountains and use a car to do so at the same time, can you?
2. BackBox
This is the name that pops up the most whenever you search for anything even remotely related to a Kali Linux alternative.
Let's just start with the fact that BackBox is free, and open-source; designed with an aim to promote IT security it has its very own software respiratory as well.
It promotes a wide array of pentesting, everything from forensic analysis, social engineering, information gathering, reverse engineering, maintenance access, documentation, reporting to hardcore exploitation is possible.
It may not be as heavily armed as Kali Linux when it comes to the number of tools, which is just around 100 at most compared to 600+ of Kali, even then it acts in its favor; helping minimize distraction while providing only the most used and important tools for Ethical hacking and testing.
Some of the tools it includes are Crunch, Metasploit, Wireshark etc. just so you know you aren't missing anything with this one.
Although in my personal opinion, Kali has more of a learning curve as compared to BackBox, the GUI still is minimal; and some friendship with Shell and scripting is demanded by both of them.
So in a nutshell, Backbox has all the potential required to be the best OS for hacking just in case Kali couldn't satisfy your needs.
3. Parrot Sec Forensic OS
Parrot Sec has quite a lot in common with Kali Linux, starting with the fact that they both are GNU based Linux distros, and obviously both of them are great pen testing tools.
One primary edge it has over Kali is its lesser use of Hardware and resources, meaning it doesn't lag that often, or loads faster and is just smoother and seamless overall.
And then again, Parrot Sec also has around 100 more tools as compared to Kali Linux when 'quantity' is taken into account, not that it really matters or makes a big dent because most of the tools available with Parrot can also be separately downloaded for Kali.
It has two versions, a 'Home' version, more light-weight, with lesser features but somewhat simpler for the common man who doesn't exactly need to be Mr. Robot.
While its other 'Security' version is the same thing overall, just with some additional features and tools which aren't available to the home version.
It has some nifty additions as well; such as a Bitcoin Wallet, Electrum (my favorite desktop Bitcoin wallet); or a complete software development environment letting you build your own projects.
Or even if it's anonymity you're looking for, it takes care of that as well by providing us with tools to get us an anonymous net surfing experience.
It may or may not be the best OS for hacking depending on how you see it; but it clearly is a more 'complete' kind of package than most other Linux pen-testing distros out there.
4. Samurai Web Testing Framework
As the name indicates, the Samurai Web Testing Framework is clearly a 'Web' testing solution.
What this means is, it too is a hacker's toolbox but it's focused more around hacking/testing websites and finding vulnerabilities in them rather than hacking into someone else's computers or cell phones.
It's like a 'package' of tools, a kind of compilation of tools needed to hack into websites, in their words, they've 'collected the top testing tools and pre-installed them to build the perfect environment for testing applications.' (Source: Sourceforge).
Also, more than an operating system such as Kali or Parrot-Sec, the Samurai Web Testing Framework is rather a virtual machine, something which runs best when run inside another operating system.
Now they may not have as many tools as Kali or Parrot Sec, but even then they're one of the best OS for hacking because in this case we're focused only around the 'web' and naturally that lowers the number of tools required.
Some of the tools included with the framework are SQLBrute, BurpSuit, SpikeProxy, RatProxy, HTTP_Print etc.
5. DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit; absolutely to the point. So, let me make it clear right here that DEFT can help you 'hack' and 'pentest'; but it's best used as a 'tracker' or 'analyzer' of sorts.
That been said, DEFT's tool-list is populated enough with advanced tools and weapons to help you become Mr. Robot given you know what you're doing and aren't a compete newbie.
In fact, even if you are a newbie, DEFT includes a guide which helps you navigate around the environment and learn some of the basics of using it.
It comes as a Live CD and is armed with WINE and LXDE which gives you the power to run Windows apps on the Linux environment.
Some of the tools it includes are Google Password Decryptor, MySQL password auditor, socket sniff, sniffpass etc.
Along with these tools which make it one of the best OS for hacking; it also includes general apps which you can run to do what most normal people do, such as LibreOffice, Gnome media player and some browsers.
6. Live Hacking OS
Live Hacking OS is a Linux based live OS which can be run directly from a CD/DVD and doesn't need any installation.
It has two versions; the full version is heavier and better, with a full graphical interface and all the available tools.
The second version has been named 'mini-CD'; and even though is equally powerful as the full version, lacks a graphical interface and is command-line only.
It totally is 'one' of the best pen-testing distro available, but in my opinion go for it only if you have super low system specs. Otherwise, Kali or Parrot should be your priority.
One of the reasons why I said that is; as a project, Live hacking OS has been 'retired'; meaning there won't be any more updates or changes to it. Although it still can be used and hasn't lost its usefulness any bit and totally deserves a mention as one of the best OS for hacking.
7. Pentoo
Based on Gentoo Linux, it surely is on every hacker, or security enthusiasts' best OS for hacking list.
It too, like all the other Linux distros here is a security and pen testing solution, and it too is available as a live CD and USB stick, so yeah no hardcore installations needed.
It supports both 32bit and 64bit infrastructures, although in addition can also be used as a Gentoo overlay.
Some of the features and tools it includes are GGPU; packet injection tools and many more. Although yes they aren't as many as Kali if 'quantity' is taken into account, but the tools are more than what most people would need, or ever use.
It also beings with itself the nightly vision for some tools in addition to GrSecurity and PAX with the Pentoo Kernal.
Bottomline, it may not be the best Linux for hacking, but without doubt is one of the top ones.
8. CyborgHawk
CyborgHawk is one of the most popular and best OS for hacking with an average 1,000 downloads per week as of today!
Not just that, when it comes to tools and feature even then it beats Kali and most other distros here with its vast arsenal of 750+ security and pen testing tools.
It too can be used from a CD or USB-stick; and as far as types of hacks, vectors or infrastructures go, let me just say that list includes just about everything.
It can be used for Wireless security, forensics, mobile security, web security, social engineering, exploitation and what not.
And obviously, the most popular and most used tools such as Metasploit, fingerprinter and everything else are packed too.
It's free, has its own respiratory, and totally supports virtual machines. Bottomline? You may even give it a try before you try Kali out!
9. Knoppix STD
Knoppix isn't something you should be using if you're totally a new resident in the Linux world, as nearly everything on Knoppix is done from the command-line.
The reason it's being listed here is because of its extremely long features and tools' list, it includes nearly every tool that any other OS boasts of in this list.
It too can be booted from a CD or USB without the need to install it, and it actually is pretty simple and 'basic' to use as long as you're familiar with Linux.
It includes Packet sniffes, TCP tools, tunnels, wireless tools, vulnerability assessment tools and basically everything else.
It totally can be used as a '
10. NodeZero
Formerly known as '
I'll call a spade a spade and make it clear that it shouldn't be compared to Kali or Backbox; it's not as massively feature-rich although with tools like Implementation 6, Implantation 6D, Toobit6, parasite 6, smurf 6, fake-mipv6 it's not entirely useless and in the right hands could wreak havoc.
It's totally capable of being used as a 'Live OS' (one which isn't traditionally installed and rather lives temporarily on the system) although its true powers are unleashed when it's installed permanently as the primary (or maybe secondary) OS.
11. BlackArc Linux
An OS crafted specially for Pentesters derived from Arch Linux is what BlackArc Linux is (the name made it kinda obvious; didn't it?)
As for the number and types of tools; it's a total feast and has an arsenal consisting of over 2154 tools! Tools for Cryptography, Debugging, Forensics, Binary, Recon, Proxy, Radio, Fingerpriting, Firmware, Networking, Cracking, Bluetooth, Windows, Tunnel, Spoofing, Packing, Keylogging and everything else in between have been included.
It also allows individual installation of these tools; or in groups saving time.Being a relatively newer project a bug may show itself now and then but the OS in itself is pretty stable and can be used for major projects.
12. CAINE
Website: https://www.caine-live.net/
CAINE is a Computer Forensic OS which stands for – Computer Aided Investigative Environment. It was primarily designed for the law enforcement agencies, military, corporate agencies or just individuals who may wish to use a computer to some of its 'extended potentials' rather than just surf the web.
It comes pre-bundled with quite a few Investigative as well as everyday-tools such as Firefox, image editors etc. It's completely open-source. There are 18 primary tools in the 'Forensic category' however each have their own sub-categories extending the number quite a bit.
Being interpolable, it (semi)-automatically compiles gathered data during a research into the final report. The interface won't be very pleasing, but that's not what you're searching for anyone are you? Although obviously it's completely graphical, with some exceptional apps requiring command-line usage.
It can be run both from a live-disk as well as be installed on the Harddisk. However, the latter isn't as straight-forward as installing Windows and may not be for everyone.
Now note that in order to use it as an OS for hacking, you may have to make some manual changes and take extra precautions as 'hacking' isn't the goal it was created with. Hence 'anonymity' is something which needs to be taken care of separately.
13. Dracos Linux
Website:https://dracos-linux.org/
Another Best OS for Hacking is Dracos Linux. It's LFS-based (Linux from Scratch). Is open-source so definitely trustworthy. Based out of Indonesia, the primary goal Dracos Linux was built with is to provide a feature-rich Pentesting tool.
Although the website requires you to have basic knowledge of what you're doing. So you won't find a 'features' list or any other marketing gimmicks explaining to you what the OS does.
Includes a plethora of tools, some of which include tools for Reverse Engineering, MITM attacks, Exploitation Testing, Analyzing Malware, Testing stress, Social Engineering etc. Basically the entire bunch which we generally expect with other similar tools.
It also mentions that no personal user data is collected which is a win and a desirable feature. The interface is another reason why we think it's not exactly beginner- friendly, it relies more on command-lines and less on GUI. But that's where the roots of hacking lie, don't they?
The one benefit which you can reap off Dracos as compared to other best hacking OS is that it has low system demands. So low-end systems can run it without lags or freezes as well.
Bottomline, give it a try if you have even the least bit of Pentesting experience and you probably won't be disappointed.
14. Network Security Toolkit
Website: https://www.networksecuritytoolkit.org/nst/index.html
Network Security Toolkit, also abbreviated as NST is a Fedora-based live OS. Or in other words, it doesn't require installations can be mounted directly from a USB stick / CD drive.
It provides extremely advanced pentesting, network and traffic monitoring tools. What's more interesting is quite a number of features that NST offers can also be accessed from a web-interface.
Some of the pre-included tools and features are Network intrusion detector, Multi-port terminal server, Multi-tap network packet capture, connections monitor, NMap, Kismet, Arp Scanning, Host/IPv4 Address Geolocation, Virtual system server etc.
Latest Mac Os
The tools are categorized into types such as Web services, Network, Security, GPS, Developer etc. These are further sub-categorized, for e.g. Web services has Browsers, Web tools, Serverlet managers, Log analyzers etc. If you're a web-dev, it also includes built in Javascript consoles and an open library.
All in all, a pretty feature-rich OS for hackers capable of getting most jobs done.
15. Arch Strike
Website: https://archstrike.org/
Arch Strike is a Linux distro designed specifically for Cyber pros and pentesters. A total of 5000+ packages are offered which let you play with the full length and breadth of hacking that there is.
Some of its features include the 'crackmapexec' package which deals with almost everything that there is about active directories. 'Wsfuzzer' automates SOAP pentesting, free proxy servers, ASP fingerprinting tool, SQL injection, info extraction from malware, payload generator, Wi-Fi injection are just some of the many other superpowers that Arch Strike offers.
It also includes an automated XSS payload generator, an XSS detection suite, a scanner for cross-site scripting, a python-based RDP etc.
Sandboxing, automatic malware behaviour analysis, JavaScript embedding in a PDF file and most other standard packages expected with one such application are available. Even fun-tools such as email harvesters, data recovery tools, steganography tools for hiding one file into another aren't amiss.
It's a LIVE-OS and can be written to USB-sticks or CD-drives. The size of the iso is 3.7GB. 'root' is the username as well as password for root access, while the normal user can login using 'archstrike'.
16. GnackTrack
Website:https://archiveos.org/gnacktrack/
GnackTrack may not be the supercharged hacking beast that Kali Linux is, however it totally qualifies as at least one of the family members.
If you're just starting out with hacking or Pentesting, GnackTrack may actually be an easier and better way to take that first step.
The interface is based on GNOME. It's completely open-source (obviously), and brings with itself a hoard of tools including metasploit, wa3f, Armitage etc. The tools have been categorized into Information Gathering, Digital Forensics, VoIP, Radio Network Analysis, and the rest has been put into Miscellaneous.
The OS can be used both with 32 bit as well as 64 bit systems. Chromium, Opera, a couple extra web browsers, FileZilla, Xchat etc. are pre-bundled.
The OS was primarily developed by a single individual and hasn't seen an update in quite some time now. Be that as it may, it still is totally functional and usable to this date.
We've listed 16 best OS for hacking so far.
That's a pretty long, and sufficient list, isn't it?
Let's try and answer some of the basics related to hacking OS then?
Which is the best OS for hacking?
Any OS can be used for hacking.
However, Kali Linux is the most widely used OS for hacking.
When not Kali, hackers still use one or the other Linux distro. Only rarely is a non-Linux environment used by serious hackers.
Why is Kali Linux good for hacking?
It offers one of the biggest arsenals (over 600) of pre-included hacking tools.
It's extremely customizable.
The primary purpose of Kali too was penetration-testing to begin with.
Is Kali Linux illegal?
No, it's not.
Kali Linux is just an operating system.
When used for illegal hacking, the illegal hacking is what's illegal not Kali Linux itself.
Are the best OS for TOR and best OS for hacking the same?
No, they aren't.
The best OS for TOR are focused on privacy and anonymity.
The best OS for hacking on the other hand bring in 'tools and techniques' to hack into other systems.
Which is the most secure OS?
There's no such thing as 'most secure OS'.
The Linux distributions are generally safer.
Insert an equation with Equation Editor On the Insert tab, in the Text group, click Object. In the Object dialog box, click the Create New tab. In the Object type box, click Microsoft Equation 3.0. The interface of Microsoft Equation Editor 3.0 free download is very straightforward and does not have any complex settings. The application is lightweight and does not take much space on the hard disk. It is also very easy to download. Microsoft Equation Editor does not have any ads making it even a better choice.
2 # Go online to check your Online Accounts through Private Browser
When you try to login into your online account such as Email Account you see a password failure. If you're feeling you're already hacked then, in this case, check your online account using a private browser. Because private browsing is safe and secure.
You can also notice if your network connection is redirected to another IP address or computer. Adobe acrobat for mac os 9 2. Lots of small hackers try to hack network to enjoy free internet but they can also remotely control your computer.
When you're browsing through the web browser you may also see an extra browser open up automatically without doing anything. If you own a domain for your website or blog you can access it after getting hacked.
3 # Anti-Virus Stop Working When Mac Computer Has Been Hacked
In Mac, if you already installed an anti-virus then this the best thing you've done to secure notebook. Oni chichi sub indo. To find out if your mac address has been hacked. You can easily check it out by scanning your Mac.
Usually, Mac users have to scan its system regularly to know if check anything usual such as the trojan virus. Trojan Virus is the virus created by hackers these viri contain backdoor or the spirits and command lines to open hidden gateways on your computer.
If you notice lots of trojan virus on your computer on the regular scan it is also a sign that your mac has been hacked.
4 # Check All Accounts Created By You on Mac Using Command Line
If you're thinking how would I know if my mac has been hacked into. Have you notice someone has seen your information and conversation on your computer. According to hackers, it is easier to hack mac in comparison to PC.
There are lots of mac terminal hack commands with the help of which hackers entered into your computer. But you can also use a command line to determine whether your Mac has been used without your authorization.
Login into your Mac OS notebook using for the regular account
Click on Applications > Utilities > Terminal
In Terminal (Command Prompt). Enter this command line 'sudo -l'.
Press Enter and then type account password and again press Enter.
Again in Terminal type following command line to open up the complete list of all accounts created on your Mac.
dscl . list /users
Press the 'Enter' button
Now you can easily check a complete list of account on your Mac OS computer. Check whether any account is created on Mac without your permission. If your mac is hacked there are additional accounts created by hackers.
In this last step, check whether an account is misused by any hacker. Type gave the following command line on Terminal
last
Hit 'Enter' now you can see each account on Mac last login date and time. Check out if there is an account which recently login without your permission.
If you've ever asked yourselves 'Which is the best OS for hacking in 2020?' than you're exactly where you should be, in your room, and on this exact page!
Security and Hacking has always been a passion of mine, and I'm sure you too have wanted to become a hacker at least at some point of your life, for some duration of time at least.
So, here I bring to you the 11 best Kali Linux Distro for hacking, well no they won't make you an expert 'hacker', that's something you'll have to work hard for, but these definitely will get you the tools and equipment you need to become so.
11 Best OS for Hacking in 2020
In case you're totally new to this, these hacking Linux distros are simply operating systems or more like versions of operating systems, locked and loaded with all the weapons you'll ever need to test the security and stability of whatever you're testing.
Try to use them to secure your computer or network rather than break into someone else's.
So here's the arsenal folks, 9 best OS for hacking (don't forget to check out #9).
1. Kali Linux
I believe not many of you here will even debate this, I mean even a hacker, who isn't a hacker, and hasn't ever wanted to be one, has heard of Kali Linux, isn't that right? It's arguably the best OS for hacking hands down!
Kali is designed and distributed by Offensive Security Ltd. as a re-write for Backtrack which was more of a forensic Linux distribution tool rather than a hacker's hammer.
Now before I say anything else, let me just say like for everything else on the planet, there are lovers, and haters for Kali, both with their own set of logics and reasons, and the 'I'm right' game goes on.
Mac Os X For Hackers
But, I personally love Kali for some basic reasons, it has 600+ pen-testing tools for starters, it's open-source, and it uses a single-root account by default, as most of the tools on Kali need highest level of privileges so it just seemed logical and time-saving (Although it has its downsides).
It's supported not only on computers with x86 wireframes, and ARM architectures, but also on smartphones including the Nexus series, One Plus One and some others!
Bottomline, Kali is designed for pen-testers and hackers; most of the tools need to be used from shell and there isn't a lot of GUI, but that's the beauty of it, you can't claim to climb the mountains and use a car to do so at the same time, can you?
2. BackBox
This is the name that pops up the most whenever you search for anything even remotely related to a Kali Linux alternative.
Let's just start with the fact that BackBox is free, and open-source; designed with an aim to promote IT security it has its very own software respiratory as well.
It promotes a wide array of pentesting, everything from forensic analysis, social engineering, information gathering, reverse engineering, maintenance access, documentation, reporting to hardcore exploitation is possible.
It may not be as heavily armed as Kali Linux when it comes to the number of tools, which is just around 100 at most compared to 600+ of Kali, even then it acts in its favor; helping minimize distraction while providing only the most used and important tools for Ethical hacking and testing.
Some of the tools it includes are Crunch, Metasploit, Wireshark etc. just so you know you aren't missing anything with this one.
Although in my personal opinion, Kali has more of a learning curve as compared to BackBox, the GUI still is minimal; and some friendship with Shell and scripting is demanded by both of them.
So in a nutshell, Backbox has all the potential required to be the best OS for hacking just in case Kali couldn't satisfy your needs.
3. Parrot Sec Forensic OS
Parrot Sec has quite a lot in common with Kali Linux, starting with the fact that they both are GNU based Linux distros, and obviously both of them are great pen testing tools.
One primary edge it has over Kali is its lesser use of Hardware and resources, meaning it doesn't lag that often, or loads faster and is just smoother and seamless overall.
And then again, Parrot Sec also has around 100 more tools as compared to Kali Linux when 'quantity' is taken into account, not that it really matters or makes a big dent because most of the tools available with Parrot can also be separately downloaded for Kali.
It has two versions, a 'Home' version, more light-weight, with lesser features but somewhat simpler for the common man who doesn't exactly need to be Mr. Robot.
While its other 'Security' version is the same thing overall, just with some additional features and tools which aren't available to the home version.
It has some nifty additions as well; such as a Bitcoin Wallet, Electrum (my favorite desktop Bitcoin wallet); or a complete software development environment letting you build your own projects.
Or even if it's anonymity you're looking for, it takes care of that as well by providing us with tools to get us an anonymous net surfing experience.
It may or may not be the best OS for hacking depending on how you see it; but it clearly is a more 'complete' kind of package than most other Linux pen-testing distros out there.
4. Samurai Web Testing Framework
As the name indicates, the Samurai Web Testing Framework is clearly a 'Web' testing solution.
What this means is, it too is a hacker's toolbox but it's focused more around hacking/testing websites and finding vulnerabilities in them rather than hacking into someone else's computers or cell phones.
It's like a 'package' of tools, a kind of compilation of tools needed to hack into websites, in their words, they've 'collected the top testing tools and pre-installed them to build the perfect environment for testing applications.' (Source: Sourceforge).
Also, more than an operating system such as Kali or Parrot-Sec, the Samurai Web Testing Framework is rather a virtual machine, something which runs best when run inside another operating system.
Now they may not have as many tools as Kali or Parrot Sec, but even then they're one of the best OS for hacking because in this case we're focused only around the 'web' and naturally that lowers the number of tools required.
Some of the tools included with the framework are SQLBrute, BurpSuit, SpikeProxy, RatProxy, HTTP_Print etc.
5. DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit; absolutely to the point. So, let me make it clear right here that DEFT can help you 'hack' and 'pentest'; but it's best used as a 'tracker' or 'analyzer' of sorts.
That been said, DEFT's tool-list is populated enough with advanced tools and weapons to help you become Mr. Robot given you know what you're doing and aren't a compete newbie.
In fact, even if you are a newbie, DEFT includes a guide which helps you navigate around the environment and learn some of the basics of using it.
It comes as a Live CD and is armed with WINE and LXDE which gives you the power to run Windows apps on the Linux environment.
Some of the tools it includes are Google Password Decryptor, MySQL password auditor, socket sniff, sniffpass etc.
Along with these tools which make it one of the best OS for hacking; it also includes general apps which you can run to do what most normal people do, such as LibreOffice, Gnome media player and some browsers.
6. Live Hacking OS
Live Hacking OS is a Linux based live OS which can be run directly from a CD/DVD and doesn't need any installation.
It has two versions; the full version is heavier and better, with a full graphical interface and all the available tools.
The second version has been named 'mini-CD'; and even though is equally powerful as the full version, lacks a graphical interface and is command-line only.
It totally is 'one' of the best pen-testing distro available, but in my opinion go for it only if you have super low system specs. Otherwise, Kali or Parrot should be your priority.
One of the reasons why I said that is; as a project, Live hacking OS has been 'retired'; meaning there won't be any more updates or changes to it. Although it still can be used and hasn't lost its usefulness any bit and totally deserves a mention as one of the best OS for hacking.
7. Pentoo
Based on Gentoo Linux, it surely is on every hacker, or security enthusiasts' best OS for hacking list.
It too, like all the other Linux distros here is a security and pen testing solution, and it too is available as a live CD and USB stick, so yeah no hardcore installations needed.
It supports both 32bit and 64bit infrastructures, although in addition can also be used as a Gentoo overlay.
Some of the features and tools it includes are GGPU; packet injection tools and many more. Although yes they aren't as many as Kali if 'quantity' is taken into account, but the tools are more than what most people would need, or ever use.
It also beings with itself the nightly vision for some tools in addition to GrSecurity and PAX with the Pentoo Kernal.
Bottomline, it may not be the best Linux for hacking, but without doubt is one of the top ones.
8. CyborgHawk
CyborgHawk is one of the most popular and best OS for hacking with an average 1,000 downloads per week as of today!
Not just that, when it comes to tools and feature even then it beats Kali and most other distros here with its vast arsenal of 750+ security and pen testing tools.
It too can be used from a CD or USB-stick; and as far as types of hacks, vectors or infrastructures go, let me just say that list includes just about everything.
It can be used for Wireless security, forensics, mobile security, web security, social engineering, exploitation and what not.
And obviously, the most popular and most used tools such as Metasploit, fingerprinter and everything else are packed too.
It's free, has its own respiratory, and totally supports virtual machines. Bottomline? You may even give it a try before you try Kali out!
9. Knoppix STD
Knoppix isn't something you should be using if you're totally a new resident in the Linux world, as nearly everything on Knoppix is done from the command-line.
The reason it's being listed here is because of its extremely long features and tools' list, it includes nearly every tool that any other OS boasts of in this list.
It too can be booted from a CD or USB without the need to install it, and it actually is pretty simple and 'basic' to use as long as you're familiar with Linux.
It includes Packet sniffes, TCP tools, tunnels, wireless tools, vulnerability assessment tools and basically everything else.
It totally can be used as a '
10. NodeZero
Formerly known as '
I'll call a spade a spade and make it clear that it shouldn't be compared to Kali or Backbox; it's not as massively feature-rich although with tools like Implementation 6, Implantation 6D, Toobit6, parasite 6, smurf 6, fake-mipv6 it's not entirely useless and in the right hands could wreak havoc.
It's totally capable of being used as a 'Live OS' (one which isn't traditionally installed and rather lives temporarily on the system) although its true powers are unleashed when it's installed permanently as the primary (or maybe secondary) OS.
11. BlackArc Linux
An OS crafted specially for Pentesters derived from Arch Linux is what BlackArc Linux is (the name made it kinda obvious; didn't it?)
As for the number and types of tools; it's a total feast and has an arsenal consisting of over 2154 tools! Tools for Cryptography, Debugging, Forensics, Binary, Recon, Proxy, Radio, Fingerpriting, Firmware, Networking, Cracking, Bluetooth, Windows, Tunnel, Spoofing, Packing, Keylogging and everything else in between have been included.
It also allows individual installation of these tools; or in groups saving time.Being a relatively newer project a bug may show itself now and then but the OS in itself is pretty stable and can be used for major projects.
12. CAINE
Website: https://www.caine-live.net/
CAINE is a Computer Forensic OS which stands for – Computer Aided Investigative Environment. It was primarily designed for the law enforcement agencies, military, corporate agencies or just individuals who may wish to use a computer to some of its 'extended potentials' rather than just surf the web.
It comes pre-bundled with quite a few Investigative as well as everyday-tools such as Firefox, image editors etc. It's completely open-source. There are 18 primary tools in the 'Forensic category' however each have their own sub-categories extending the number quite a bit.
Being interpolable, it (semi)-automatically compiles gathered data during a research into the final report. The interface won't be very pleasing, but that's not what you're searching for anyone are you? Although obviously it's completely graphical, with some exceptional apps requiring command-line usage.
It can be run both from a live-disk as well as be installed on the Harddisk. However, the latter isn't as straight-forward as installing Windows and may not be for everyone.
Now note that in order to use it as an OS for hacking, you may have to make some manual changes and take extra precautions as 'hacking' isn't the goal it was created with. Hence 'anonymity' is something which needs to be taken care of separately.
13. Dracos Linux
Website:https://dracos-linux.org/
Another Best OS for Hacking is Dracos Linux. It's LFS-based (Linux from Scratch). Is open-source so definitely trustworthy. Based out of Indonesia, the primary goal Dracos Linux was built with is to provide a feature-rich Pentesting tool.
Although the website requires you to have basic knowledge of what you're doing. So you won't find a 'features' list or any other marketing gimmicks explaining to you what the OS does.
Includes a plethora of tools, some of which include tools for Reverse Engineering, MITM attacks, Exploitation Testing, Analyzing Malware, Testing stress, Social Engineering etc. Basically the entire bunch which we generally expect with other similar tools.
It also mentions that no personal user data is collected which is a win and a desirable feature. The interface is another reason why we think it's not exactly beginner- friendly, it relies more on command-lines and less on GUI. But that's where the roots of hacking lie, don't they?
The one benefit which you can reap off Dracos as compared to other best hacking OS is that it has low system demands. So low-end systems can run it without lags or freezes as well.
Bottomline, give it a try if you have even the least bit of Pentesting experience and you probably won't be disappointed.
14. Network Security Toolkit
Website: https://www.networksecuritytoolkit.org/nst/index.html
Network Security Toolkit, also abbreviated as NST is a Fedora-based live OS. Or in other words, it doesn't require installations can be mounted directly from a USB stick / CD drive.
It provides extremely advanced pentesting, network and traffic monitoring tools. What's more interesting is quite a number of features that NST offers can also be accessed from a web-interface.
Some of the pre-included tools and features are Network intrusion detector, Multi-port terminal server, Multi-tap network packet capture, connections monitor, NMap, Kismet, Arp Scanning, Host/IPv4 Address Geolocation, Virtual system server etc.
Latest Mac Os
The tools are categorized into types such as Web services, Network, Security, GPS, Developer etc. These are further sub-categorized, for e.g. Web services has Browsers, Web tools, Serverlet managers, Log analyzers etc. If you're a web-dev, it also includes built in Javascript consoles and an open library.
All in all, a pretty feature-rich OS for hackers capable of getting most jobs done.
15. Arch Strike
Website: https://archstrike.org/
Arch Strike is a Linux distro designed specifically for Cyber pros and pentesters. A total of 5000+ packages are offered which let you play with the full length and breadth of hacking that there is.
Some of its features include the 'crackmapexec' package which deals with almost everything that there is about active directories. 'Wsfuzzer' automates SOAP pentesting, free proxy servers, ASP fingerprinting tool, SQL injection, info extraction from malware, payload generator, Wi-Fi injection are just some of the many other superpowers that Arch Strike offers.
It also includes an automated XSS payload generator, an XSS detection suite, a scanner for cross-site scripting, a python-based RDP etc.
Sandboxing, automatic malware behaviour analysis, JavaScript embedding in a PDF file and most other standard packages expected with one such application are available. Even fun-tools such as email harvesters, data recovery tools, steganography tools for hiding one file into another aren't amiss.
It's a LIVE-OS and can be written to USB-sticks or CD-drives. The size of the iso is 3.7GB. 'root' is the username as well as password for root access, while the normal user can login using 'archstrike'.
16. GnackTrack
Website:https://archiveos.org/gnacktrack/
GnackTrack may not be the supercharged hacking beast that Kali Linux is, however it totally qualifies as at least one of the family members.
If you're just starting out with hacking or Pentesting, GnackTrack may actually be an easier and better way to take that first step.
The interface is based on GNOME. It's completely open-source (obviously), and brings with itself a hoard of tools including metasploit, wa3f, Armitage etc. The tools have been categorized into Information Gathering, Digital Forensics, VoIP, Radio Network Analysis, and the rest has been put into Miscellaneous.
The OS can be used both with 32 bit as well as 64 bit systems. Chromium, Opera, a couple extra web browsers, FileZilla, Xchat etc. are pre-bundled.
The OS was primarily developed by a single individual and hasn't seen an update in quite some time now. Be that as it may, it still is totally functional and usable to this date.
We've listed 16 best OS for hacking so far.
That's a pretty long, and sufficient list, isn't it?
Let's try and answer some of the basics related to hacking OS then?
Which is the best OS for hacking?
Any OS can be used for hacking.
However, Kali Linux is the most widely used OS for hacking.
When not Kali, hackers still use one or the other Linux distro. Only rarely is a non-Linux environment used by serious hackers.
Why is Kali Linux good for hacking?
It offers one of the biggest arsenals (over 600) of pre-included hacking tools.
It's extremely customizable.
The primary purpose of Kali too was penetration-testing to begin with.
Is Kali Linux illegal?
No, it's not.
Kali Linux is just an operating system.
When used for illegal hacking, the illegal hacking is what's illegal not Kali Linux itself.
Are the best OS for TOR and best OS for hacking the same?
No, they aren't.
The best OS for TOR are focused on privacy and anonymity.
The best OS for hacking on the other hand bring in 'tools and techniques' to hack into other systems.
Which is the most secure OS?
There's no such thing as 'most secure OS'.
The Linux distributions are generally safer.
Insert an equation with Equation Editor On the Insert tab, in the Text group, click Object. In the Object dialog box, click the Create New tab. In the Object type box, click Microsoft Equation 3.0. The interface of Microsoft Equation Editor 3.0 free download is very straightforward and does not have any complex settings. The application is lightweight and does not take much space on the hard disk. It is also very easy to download. Microsoft Equation Editor does not have any ads making it even a better choice.
Did you know Windows 10 is extremely unsafe, risky and nosy? (Here are some Windows 10 privacy tools).
Parrot OS vs. Kali Linux: Which is better?
I've found this to be a question asked quite frequently by those searching for the best hacking OS.
Well, in simpler terms, if you need a less feature-rich but updated hacking OS, Parrot OS is the answer.
But, if you need more control with customization, better injection abilities, better hardware support and support for multiple languages, you should go with Kali Linux.
However, because Parrot OS is comparatively lightweight, it can be used even on a bit outdated or low-spec devices.It can be run on just 320MB RAM and 16GB space.
On the other hand, Kali is a bit more demanding. You'll need at least 1GB RAM and 20 GB storage. Obviously, I doubt any of you reading these have systems lower than these specs anyway.
Just in my personal opinion, it may help going with Parrot OS if you're an absolute beginner. Once you get the hang of things, the switch can be made.
Note that the features are largely the same. It's just the interface and overall UX which differs to some extent.
Final Words
So that's a wrap as far as this piece on the best OS for hacking goes folks. I believe I've listed the world's most popular, most used, and feature-rich OS used for hacking, or security forensics.
Know that using none of these tools is as easy as they show in the movies, so you can't just hack your block's power grid on day one or something, but eventually, these tools totally have the potential and the features to make that happen.
Obviously considering all of these are Linux distros, you'll need at least basic knowledge of Linux before you actually unleash the true potential of these beasts.
Anyway, note that these best OS for hacking are shared here purely for educational purposes, any proper or improper use of them is totally your responsibility and me or anything or anyone else associated with me can't be held liable for your actions.
That been said, also remember that downloading, or even using these tools is completely legal, as long as you do not harm anyone else in any way.
Do let me know what you think of this piece and the tool on our Facebook page, hearing from you folks means a lot.
